What is Hacking?
The word 'hacking' has several meanings, but in the context of ICT, it is normally taken to mean breaking in to a computer system.
Why Do Hackers Hack?
A hacker may break into a system just out of curiosity or for the challenge - can they get through the system’s defences? But, it is more likely that they are breaking in to access data, usually because the data has value.
For example, if a hacker enters your computer and steals financial information such as your credit card number, or the password to your bank account, they could use that information to make purchases.
For example, if a hacker enters your computer and steals financial information such as your credit card number, or the password to your bank account, they could use that information to make purchases.
Can a Computer be Protected from Hacking?
Just as in the real world, there is no guaranteed way to stop someone breaking into a building (you can make it very difficult, but every security system has its weaknesses), there is also no guaranteed way to stop someone breaking into a computer system.
However, you can make it difficult enough so that a hacker moves onand looks for an easier target.
You should:
However, you can make it difficult enough so that a hacker moves onand looks for an easier target.
You should:
- Use strong passwords to protect your user login account
- Never reveal your login password to anyone else
- Place a firewall between your computer and any network
- Disconnect from networks when you are not using them
- Encrypt any sensitive information (just in case they get in)
What is Malware?
Malware is short for malicious software.
Malware is the name given to any software that could harm a computer system, interfere with a user's data, or make the computer performactions without the owner's knowledge or permission.
Basically malware is software that you really don't want to have on your computer!
People can end up with malware installed on their computer system in a variety of ways:
- Installing software that seems ok, but has malware hidden inside(know as a 'Trojan Horse').
- Having their computer hacked, and the software installed by the hacker.
- Visiting dodgy websites and clicking on infected links
- The computer being infected by a computer virus
 Some examples of malware:
Some examples of malware:
- Spyware (spys on you)
- Adware (pops up adverts all the time)
- Root kits (allows a hacker full access to your computer)
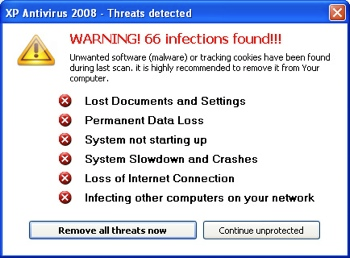
Ironically, one of the most infamous bits of spyware around is calledAntivirus XP 2008/9.
This software is advertised as a genuine anti-virus product (for free too!), but if you install it, you've actually installed some malware.
The software will 'scan' your computer, then tell you that your computer is infected. You'll then be bullied with endless pop-ups into paying a fee to have your computer 'disinfected'.
In fact the only infection you really have is the fake anti-virus!
It is estimated that the creators of this malware have made millions of dollars from innocent, gullible computer users.
It's best to assume that if software is given away for free, there is probably something dodgy about it - Use Google to check any software out before downloading and installingSo, What is a Computer Virus?
A computer virus is a piece of software that can 'infect' a computer (install itself) and copy itself to other computers, without the users knowledge or permission.
Most computer viruses come with some kind of 'payload' - the malwarethat does something to your computer.
For example, the virus might install some spyware (software that watches what you do with your computer), it might search your computer for credit card information, or it might install software that gives someone remote control of your computer (turning it into a 'zombie').
How Can a Computer Be Protected from Viruses?
There are some simple things you can do to help prevent a virus infecting your computer:
- Install anti-virus software and keep it up-to-date (this is the most important thing you can do!)
- Install anti-malware software (stops software installing without your knowledge)
- Never download and install software from the Internet unless you are certain it is from a source you can trust
- Don’t open e-mail attachments unless you have scanned them (even a file that seems to be a picture can contain a virus)
- Don’t click links in websites that seem suspicious (if a site is offering prizes / free stuff / etc. be suspicious!)
- If someone gives you a memory stick or CD-ROM, run a virus scan on it before opening any files.
- Don’t trust cracked versions of software from file-sharing sites (often these have viruses and other malware added to them - a Trojan horse)










No comments:
Post a Comment